Five Components of Identity Protection
In a previous blog, I wrote about Identity Protection, the framework which leads to better prevention, detection and remediation of identity theft. Here, I want to go into the components of Microsoft’s ecosystem which contribute to Identity Protection.
1 Microsoft Identity Manager – MIM
Let’s start with the basics. No organization’s systems can be secure if it does not know who has access, who should have access but doesn’t, and, most importantly in this context, who has access but should not. Microsoft Identity Manager provides functionality to synchronize data from, say, an authoritative HR system in such a way that accounts are created and disabled in a timely and accurate.
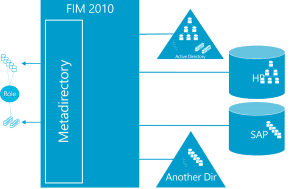 Groups (ie permissions) might be managed too, perhaps using MIM’s portal (not shown above), and Oxford Computer Group (amongst others) can provide software products which extend the out of the box MIM functions to more formal support of access management (including RBAC and attestation) with modern HTML5 portals, allowing organizations to use MIM for comprehensive Access Management.
Groups (ie permissions) might be managed too, perhaps using MIM’s portal (not shown above), and Oxford Computer Group (amongst others) can provide software products which extend the out of the box MIM functions to more formal support of access management (including RBAC and attestation) with modern HTML5 portals, allowing organizations to use MIM for comprehensive Access Management.
2 Azure AD Connect
MIM, in conjunction with its sister product Azure AD Connect (which is based on the same synchronization engine and is therefore very familiar to MIM practitioners), can ensure that the good management you have configured on premises, can be extended into the cloud. 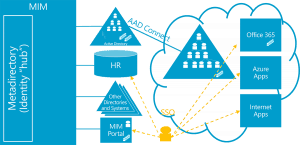 By synchronizing on-premises and cloud uses and groups, you can arrange that your users have appropriate access to your cloud properties and a well as your on-premises systems.
By synchronizing on-premises and cloud uses and groups, you can arrange that your users have appropriate access to your cloud properties and a well as your on-premises systems.
3 Multi-Factor Authentication – MFA
Once the basics of sound identity and access management are in place, we need to concentrate on making the identities trustworthy – it does not help to have beautifully managed access permissions if an attacker can guess passwords and make use of these beautifully managed permissions. The approach to improving the trustworthiness of identities which has become most accepted is the use of Multi-Factor Authentication, which adds additional factors to the password to ensure that the user is who they say they are. In corporate environments one such factor is commonly based on cryptographic certificates (on hardware- or software-based smartcards).
A more general approach is MFA based on one-time tokens or phone calls. In this system, the user is prompted, during logon, to provide a code which is generated by a smartphone app, or sent by SMS to their pre-registered mobile phone number. For those cases where no smartphone or mobile is available, a call can be made to a desk phone (again, under a pre-registered number) and the user must answer the call and press “#” to confirm that it is indeed they who are logging in.
Microsoft’s MFA system supports cloud and on-premises authentications, and can be configured to step up from single to multi-factor authentication under various circumstances (for example for elevated users, for particular applications, or on detection of anomalous behaviour. It is a key part of the Identity Protection Framework.
4 Privileged Identity Management and Privileged Access Management (PIM and PAM)
This is a subject about which I have written blogs and white papers before, so I will keep it concise here. A favorite route for attackers to gain unrestricted access to systems and their valuable data is via the theft of administrative credentials. Apart from using MFA to provide additional trustworthiness to administrative logins, the best way of reducing the likelihood of admin credentials being stolen is simply to have fewer of them at any time.
The principle behind Privileged Identity/Access Management (PIM and PAM respectively) is that the user accounts of our human administrators only have administrative permissions for the period when they are actively performing some administrative tasks, and only those permissions they actually need to in order to perform them. This involves the user requesting elevated permissions before attempting administration tasks (and this elevation may involve MFA or even, in high-assurance environments, approval), and they then perform admin tasks with a short-lifetime token which, once its lifetime expires, is not worth stealing.
Microsoft offers PIM/PAM for both cloud and on-premises systems: PIM for Azure Active Directory, securing Office 365 and AAD-connected applications; and PAM (part of the MIM suite) for on-premises Active Directory-based systems.
5 Threat Detection with Advanced Threat Analytics and Cloud App Security
The above measures contribute to the prevention and remediation of successful attacks – so now we need to talk about detection. But first, take a a moment to consider these facts:
- 200+ days is the median number of days attackers stay within a network before detection
- $3.5 million is the average cost of a data breach to a company (Source: Ponemon Institute Release 2014 Cost of Data Breach)
- One in five small and medium businesses are targeted in cybercrime attacks (Source: National Cyber Security Alliance)
Attacks by professional criminals do not just happen – they are extensively planned and prepared. First, an attacker needs to understand the environment they are trying to attack – which domains, accounts, servers etc. are in the environment. This reconnaissance process involves broad querying of directories and attempted anonymous access to a variety of endpoints. Once an attack target has been established by reconnaissance, the attacker will commonly attempt to gain an initial foothold by attacking a low-value (and therefore perhaps poorly-monitored) account using a phishing or social engineering attack to obtain a password or to steal access tokens directly from a workstation. Once in control of this low-level account, the attacker must attempt to access further systems (‘lateral movement’) with a view to gaining access to more privileged credentials (‘privilege escalation’).
Reconnaissance, lateral movement and privilege escalation are all activities which are different from ‘normal’ user actions in the network. Microsoft’s Advanced Threat Analytics monitors your LDAP and Kerberos traffic on the network. First, it establishes what is ‘normal’ – which users in which departments access which servers and resources at what time from what workstations – then it is in a position to detect and alert us to the ‘abnormal’.
A similar detection role is played by Microsoft’s Cloud App Security. This product collects information from your Proxies and Firewalls to establish patterns of usage, and then compares future activity against these patterns to detect anomalies and suggest actionable remediation.
The five components mentioned in brief here are fully fledged and comprehensive products. Individually, they are powerful. Together, they offer state-of-the-art identity protection.
Start your investigation of how these components can help secure your environment, and talk to Oxford Computer Group!