Moving Towards Zero Trust with an ICAM Solution Architecture
Meet the New Federal Zero Trust Mandate with an ICAM-focused architecture developed by Saviynt, Microsoft, and OCG Federal.
Lately, it seems like everyone is talking about Zero Trust— and for a good reason. It is a strategy, mindset, and architecture that provides a dynamic way to protect against external cyber threats and insider threats.
The rising concern about cybersecurity breaches is nothing new, but recent events highlight the urgent need to adopt new strategies to secure the public sector. Breaches are growing by the day and becoming substantially more damaging — both in impact and disruption. Worse, they stand to put federal agencies’ missions at risk as they aim to exfiltrate data and halt critical operations. That’s why it is imperative to understand that there are two crucial elements of most breaches: a combination of credential compromise and privilege escalation.
Today, we’ll explore the move to Zero Trust using your existing security technology (and new identity solutions) to address these challenges head-on with an ICAM-focused Zero Trust reference architecture developed by Saviynt, Microsoft, and OCG Federal.
Zero Trust and the Impact of the Cyber Executive Order
Zero Trust is more than any one technology. And to fully embrace it, you’ll need to redefine your entire approach to identity and security to protect your people, IT infrastructure, and sensitive assets.
In short, Zero Trust moves from implicit trust to a continuous re-evaluation of risk and trust levels. It protects the entire IT ecosystem, accelerates digital transformation, and secures the remote workforce. In practice, it translates into security architecture and a series of process improvements that start with a simple assumption: Act as if a breach is imminent or already occurred.
The recent Executive Order on Improving the Nation’s Cybersecurity demonstrates a welcomed focus on cybersecurity as a national security issue. Cyber threat actors — both nation-state and criminal — are direct threats to society and individuals alike. The Executive Order (EO) focused on several key areas:
- Improving the collaboration between the Federal government and the private sector
- Leveraging cloud services such as Software as a Service (SaaS), Infrastructure as a Service (IaaS), and Platform as a Service (PaaS)
- Implementing a Zero Trust Architecture
- Software supply chain security
The order directs several federal agencies to review existing policies and rules to eliminate blockers and legal constraints on sharing information between companies, vendors, and the federal government. It also details actions related to Software Supply Chain Security that are also important.
Moving to a Zero Trust Identity Architecture
Embracing Zero Trust at your agency requires adopting “identity” as the new security perimeter. In doing this, you don’t necessarily have to replace any existing technologies. Instead, you can leverage existing technology and bolster your security posture with a pivot towards “Least Privilege and Cyber Risk Reduction.”
Zero Trust Identity is the practical application of identity to support and strengthen Zero Trust principles. It requires a continuous risk and trust assessment every time access is attempted using contextual identity information to inform and optimize access policies. This also supports the principle of least privilege and granting access to the right entities, for the right reasons, for the right amount of time.
In the recent executive order, the Administration outlines its position on Zero Trust Architectures. This includes the security controls and access processes that agencies must implement to meet the mandate.

In practice, this means your agency needs to implement the following steps:
- Eliminate implicit trust across elements, nodes, or services and adopt continuous verification
- Adopt Just-Enough access capabilities to grant the bare minimum access to complete a job
- Implement granular, risk-based controls and security automation to protect data and infrastructure from threats in real-time
- Apply the principle of least privilege for every access decision. Deny access to resources based on the combination of several risk attributes
Embracing Least-Privileged Access
With identity as your new security perimeter, you can execute the second part of a successful Zero Trust strategy. This is the concept of “least-privileged access.”
Let’s start by agreeing on the fact that you cannot govern what you cannot see. In addition, the traditional access request or user provisioning process lacks in its ability to show operators potential risks they may be allowing or potential toxic combinations of access. As the EO states, “users’ access should be based on allowing full access – but only to the bare minimum they need to perform their jobs.” Pivoting to least privilege with continuous monitoring and ongoing governance is a critical component of Cyber Risk reduction.
Implement New ICAM-Focused Zero Trust Architecture
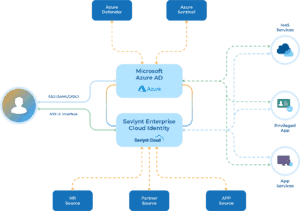
 OCG Federal, Saviynt and Microsoft have developed an ICAM-focused Zero Trust reference architecture aimed at enabling you to move in these directions. The reference architecture leverages critical pre-integrated capabilities available in Microsoft and Saviynt to provide a modernized identity infrastructure. It leverages Azure Active Directory (AAD) as the single authoritative identity store.
OCG Federal, Saviynt and Microsoft have developed an ICAM-focused Zero Trust reference architecture aimed at enabling you to move in these directions. The reference architecture leverages critical pre-integrated capabilities available in Microsoft and Saviynt to provide a modernized identity infrastructure. It leverages Azure Active Directory (AAD) as the single authoritative identity store.
Agencies that use Microsoft M365 are already utilizing this identity store as their authoritative identity source for Microsoft cloud services.
If you would like to discuss this reference architecture in more detail, please reach out to us at ZT@OCGFederal.com. You can find more information about OCG Federal here.