Identity Protection – what can we do?
Identity is central to modern computing.
Knowing that the user trying to access information or services is the person they claim to be is the cornerstone of commerce, corporate collaboration, and many other facets of modern life.
Not coincidentally, the efforts made by criminals to steal an identity with a view to impersonating its true owner have increased dramatically. No longer are script kiddies at work, who just want to see what is possible – modern identity theft is a multi-million dollar business with tools and starter kits available for the right price.
And it’s getting worse!
Protecting against the theft of identity is therefore the first priority for the security-minded. In the closed, private network world, much effort was focused on the appropriate creation and removal of user accounts, with appropriate permissions added and revoked over time. Smartcards and password management approaches added assurance that the user was indeed who they said they were. This was an approach to the orderly management of identities, but the new generation of threats means that even well-managed identities can be stolen, with the use of cached-token theft, social engineering, and phishing.
So what can we do about it?
As well as good management, therefore, detection of theft (whether attempted or successful) is essential, and this is increasingly an area of focus for Microsoft, and therefore also of Oxford Computer Group, as one of Microsoft’s leading partners in the provision of secure and well-managed identity systems.
Microsoft provides protections for your cloud-related activity (such as Office 365) as well as for activity on an internal network. The narrative which follows applies to the cloud protections, but similar principles apply to risk detection in your private network.
Detecting suspicious behavior
The shadowy nature of identity theft means that certainty is a rare commodity, so the evaluation of the threat must be on a risk basis – the more suspicious elements pointing to an attack are detected, the higher risk can be assigned to an attempted access, and this risk-based approach is precisely Microsoft’s approach. Using the billions of authentications made each day to the Microsoft Azure Active Directory which is at the core of Office 365, Hotmail, Xbox and other Microsoft properties, Microsoft has a vast amount of evidence on which to base an evaluation of “normal” versus “suspicious” behavior, so that a risk score can be assigned.
Responding to threats
The ‘scales of grey’ risk scoring which result from this machine learning-based analysis is only half the story. The response to a detected threat is equally important, which requires both notification and remediation. First, administrators must be notified that an identity is at risk of having been compromised, and Microsoft’s Identity Protection delivers immediate notification as well as weekly summaries, including as much information specific to the nature of the threat to the identities as possible, for example, that a login was attempted from a known bot-net host. Second, action must be taken – and a variety of remediation steps are available. Most importantly, policy-based, automated remediation is configurable, so that accounts which are under attack are immediately protected. The user might be blocked from login; required to use Multi-Factor authentication; to reset their password; or the user might also be required to use MFA for all future logins.
In addition to these automatic remediation, the administrator can use their judgement to apply similar remediation, and they can also reset the user’s password.
Assessing risk
The policies which govern these automatic protections use a risk scale, which is evaluated based on the severity of the issue detected, coupled with the confidence in the detection algorithm that this issue is indeed present.
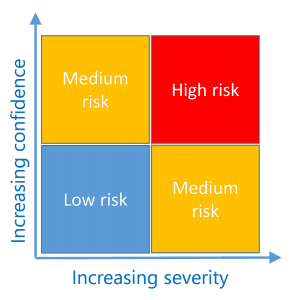
The overall risk score for a user is an aggregation of all the relevant risk issues which have been detected – therefore it is important that the issues are marked as Resolved (if they are) so that the user’s risk score can be returned to a more normal level. Therefore, the issues raised in the analysis are tracked so that the administrator can investigate each issue and mark each appropriately once the issue is resolved.
Informing the user
If a user’s account is at risk, the user is notified at logon (depending on the client being used and whether this client is Identity-Protection aware). The language explains that some anomalous behavior has been found, and that therefore certain steps (as determined by policy) have been taken to protect the account. Note that the risk evaluation is performed both in real-time and asynchronously – so detection can be delayed by 2-4 hours after anomalous events take place.
What next?
Understanding the risks and remediations of identity theft is extremely important. Various different system components come together to provide this degree of insight into the security posture of your organization – from Multi-Factor Authentication to Privileged Identity Management – and Oxford Computer Group is in a unique position to assist you in the evaluation of these components and their collective configuration to make strides in securing your organization.