What is Conditional Access Authentication Strength?
The natural world has taught us that you either adapt or die. Hundreds of species, both plant and animal, have been very successful at adapting to their changing landscape, whether it is caused by climate change, habitat loss or to avoid becoming lunch. As an example, Meerkats that inhabit the African savanna, where predators abound, can scan long distances across their desert homes. Due to the dark patches of fur surrounding their eyes, the sun glare is not a problem. They can see danger coming from every angle – often even before the predators have spotted them!
When it comes to your digital landscape, it is also vital to adapt to persistent, ever-changing threats. Hackers do not give up when new security measures are put in place, so those responsible for defending the digital assets of an organization must be vigilant and flexible. This includes protecting identities.
The First Step: Enabling Multi-Factor Authentication
For years we have heard the drumbeat about the importance of enabling multi-factor authentication (MFA). According to the 2022 Verizon Data Breach Investigation Report, over 40% of breaches were due to stolen or misused credentials. The summary of findings states, “The human element continues to drive breaches. Whether it is the use of stolen credentials, phishing, or simply an error, people continue to play a large part in incidents and breaches alike.”
Many organizations have responded by enabling MFA for all identities accessing resources across the digital estate. As the statistics show, enabling MFA reduces credential-based attacks by 99.9%. Well, that was at least true when the statistic was published by Microsoft in 2019. Since then, attackers have adapted.
While any MFA is better than no MFA, not all MFA is created equal. SMS-based MFA has long been susceptible to SIM slamming attacks which prompted many organizations to switch to software OATH tokens and authentication apps. The convenience of these apps has helped organizations adopt MFA, since a sizable percentage of enterprise users already have personal or corporate-issued mobile devices. This makes deployment of app-based MFA seamless. To make authentication as easy as possible for users, many organizations have opted to use push verification as the primary authentication method. But again, the attackers have adapted their methods.
The terms “MFA fatigue” aka “MFA push spam” have now entered the parlance. An MFA fatigue attack refers to “…when a threat actor runs a script that attempts to log in with stolen credentials over and over, causing what feels like an endless stream of MFA push requests to be sent to the account’s owner’s mobile device.” This type of social engineering attack has proven to be successful recently. The Lapsus$ and Yanlouwang threat actors successfully breached large enterprises such as Microsoft, Cisco, and Uber. So, blue team defenders must adapt or die.
Organizations leveraging Microsoft Entra Azure Active Directory as their identity provider with a Premium P1 license or higher can harden their MFA controls by enabling number matching and additional context. This prompts users to enter the number displayed on the screen. It also provides users with information on the application and geographic region where the prompt originates from. These two features can drastically reduce the potential for phishing and other social engineering attacks. However, more robust approaches may be required to help protect the most sensitive users (e.g., C-suite, Finance, privileged accounts) and the resources they access.
Conditional Access Authentication Strength
Conditional Access Authentication Strength policies can provide this additional layer of protection. This new feature of Microsoft Entra Azure Active Directory allows identity teams to specify the combination of authentication methods that can be used to access a resource.
For example, administrators can make only phishing-resistant authentication methods the default for high value accounts or for accessing highly sensitive resources such as identity systems, human resources systems, or financial applications. Phishing-resistant methods can include FIDO2 security keys, Windows Hello for Business, or certificate-based authentication (as a secondary authentication factor).
There are three built-in authentication strengths that can be used as-is with existing or new conditional access policies. Custom policies can also be created. The below table details the authentication combination methods available and the built-in policies they are enabled for.
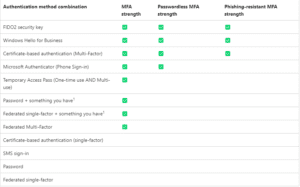
The user experience for resources protected by authentication strength policies depends on several factors:
- Which authentication method was previously used?
- Which methods are available for the authentication strength?
- Which methods are allowed for user sign-in in the authentication methods policy?
- Is the user registered for any available method?
If a user initially signs in and authenticates using password + push verification and attempts to access a resource protected by the “MFA strength” policy, they can do so without another authentication prompt. However, if they attempt to access a different resource, such as a sensitive application that is protected by the “phishing-resistant MFA strength” policy, they will be prompted to provide one of those methods, i.e., Windows Hello for Business or a FIDO2 security key.
If the user has not registered a method that satisfies the required authentication strength, they are redirected to the combined registration page. If the authentication strength does not include a method that the user can register and use, they are blocked from accessing the resource.
This is just one example of how Authentication Strength can be leveraged. In the ongoing fight to protect critical and sensitive data, it is another tool that will help improve the overall security posture of enterprises.
Get Started with Microsoft Entra and Conditional Access Authentication Strength
As a premier identity and security Microsoft Partner, Oxford Computer Group regularly conducts “Secure Identities and Access” workshops, which can provide your organization with a deep understanding of Microsoft Identity and identity modernization. We will be happy to discuss the details with you. Contact Us.
More Microsoft Entra Resources:
- Using Microsoft Entra Verified ID for Identity Proofing of Partners, Customers, and Employees (webinar January 26th)
- What You Need to Know About Microsoft Entra (blog)
- Multicloud Permissions Management using Microsoft Entra (webinar recording)