Why A Strong Identity Strategy is Vital for Health
Healthcare organizations worldwide are increasingly making front page news for all the wrong reasons.
Hacking and ransomware attacks are sadly on the rise – and they are hitting health care organizations hard.
Just this week, hospitals in the UK suspended their email servers in a precautionary measure against a phishing scam, and just over a month ago, the global WannaCry cyber attack crippled the UK’s National Health Service.
Over 130 US healthcare organizations have suffered major breaches so far in 2017
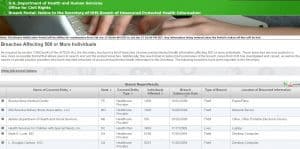
In the US, 1,953 healthcare organizations appear on the Department of Health and Human Services’ Breach Portal which records breaches of unsecured protected health information that have affected 500 or more individuals. And over 130 organizations have joined the list so far this year.
Email is one of the most common sources of attacks
It’s interesting to see how regularly email appears in the “Location of Breach” column. This is usually from a phishing attack that inserts malware, often injected through a compromised identity, helped by incorrectly patched and/or out of date software and dormant accounts.
Helping healthcare organizations to protect themselves against such attacks is a key – and fast growing – area of work for Oxford Computer Group. Not only do our customers want to keep confidential patient information safe, cleaning up the post-attack mess and paying associated fines is a very costly business!
Lack of identity strategy is the key issue
We consistently find that the main issue is not a lack of virus detection software or other approaches to security, but a lack of strategy on how to manage a very dynamic population of staff, contractors, and business partners that access data both on-premises and in the cloud. A lot of it is plain-old-simple lifecycle management of identity and access, ensuring that ONLY the right people get access to the right information.
Our expert consultants can help with both strategy and implementation. From business processes to technical tools, we are all about building a manageable approach to identities that will keep the data those identities access secure.
Let us help your organization to stay off the breach list!
If you need an expert technical partner to guide you safely through all the options as you take advantage of what the Microsoft cloud offers, look no further than Oxford Computer Group. We offer award-winning consulting and training to organizations throughout the world.