Saviynt Advanced Access Reviews: Capabilities and Definitions
The periodic review of access assigned to person and non-person accounts is a critical component and practice for Identity Governance and Administration (IGA) to maintain compliance and enforce least privilege.
With the constant increase of applications being used within organizations, the task of reviewing access is a time-consuming process that often lacks supporting metadata and accurate business-friendly descriptions of access. These issues within the access review process often lead to fatigue and rubber stamping of certifications. Saviynt Security Manager’s (SSM) advanced access review capabilities give organizations the flexibility to target access reviews effectively.
I recently completed a project that was primarily focused on implementing access reviews for SOX compliant applications. To remain in compliance with SOX, access reviews were done manually – a labor-intensive and error-prone process involving many spreadsheets and emails to business owners and managers. This process placed a significant burden on the IT personnel, business owners, and manager and impeded user productivity and organizational agility. My goal was to provide that same level of flexibility and customization with a more streamlined and automated approach to doing the access reviews while providing a better user experience for the certifiers. As I worked to implement these access review in SSM, I was impressed with the capabilities that SSM provided to meet these requirements.
The below sections describe some of the advanced access review capabilities available in SSM. In SSM, the access review capabilities are referred to as campaigns. You will see the word access review and campaign used interchangeably in this blog.
Campaign Types | Applications to Review | Objects to Certify | Advanced Campaign Configurations | Campaign Templates | Certification Launch | Event-based Certifications | Context and Filtering During Review | Certifier Response Options During Review | Exporting Campaign Results | Summary
Campaign Introduction
In SSM the campaign feature was introduced to simplify and group similar certification types. The benefit of using a campaign is that instead of launching individual certifications, it provides an alternative to have a single campaign with multiple certifications encompassed within the single campaign. This helps to easily monitor and take actions on all the certifications that are part of the campaign.
Campaign Types
SSM provides different campaign types to provide the flexibility on what access is being reviewed and who is reviewing the access. The campaign types listed below are for reviewing access in applications.
Application Owner – The application owner is setup as the certifier to review and certify user’s base accounts, entitlements, and roles associated with the application. Each reviewer in the certification of this type is focused on one specific application. Primary and secondary application owners can be set on a per application basis.
User Manager – The manager is setup as the certifier to review their direct report’s base accounts, entitlements, and roles. Manager and secondary manager can be set on a per user basis. Within a campaign, there would be a certification setup for each manager or secondary manager that included their direct report’s access in one or more applications.
Service Account – The service account owner is setup as the certifier to review the service account’s base account, entitlements, and roles. This campaign type is responsible for certifying access assigned to service accounts within applications. Service account types are assigned on a per application basis. Primary and secondary service account owners are set on a per account basis.
Entitlement Owner – Used by entitlement owners to review the entitlements, child entitlements, and base accounts associated with those entitlements. This campaign type is responsible for certifying access on a per entitlement basis. A primary and secondary entitlement owner is set on a per entitlement basis.
Applications to Review
SSM provides the capability of launching an access review campaign that targets a single, multiple, or all applications represented in SSM.
All – Targets all applications configured within SSM.
Single – Targets by name one applications configured within SSM.
Multiple – Targets by name more than one application configured within SSM.
Objects to Certify
SSM provides the capability to choose the object types to certify within a campaign.
Account – The base account within an application.
Entitlement – The permissions withing an application associated with the base account.
Emergency Access Role – Roles that consist of emergency access needed within an application for a short period of time.
Enterprise Role – Roles that consist of one or more entitlements across multiple applications.
Application Role – Roles that consist of one or more entitlements within a single application.
Advanced Campaign Configurations
SSM provides the capability to be even more granular on what is pulled into an access review by allowing you to define custom queries. The custom queries parameters available are based on the campaign type selected. Below are the most common custom query parameters:
Users Query – This query allows you to target only a subset of users to be reviewed within the certification. For example, you can create a query that only pulls in users from a specific department like Finance for review.
Account Query – This query allows you to target only a subset of base accounts to be reviewed within the certification. For example, you can create a query that only pulls in base accounts that are active for review.
Entitlement Query – This query allows you to target only a subset of entitlements to be reviewed within the certification. For example, you can create a query that only pulls in privileged entitlements into the review.
Campaign Templates
While creating a campaign in SSM, you can define the campaign configurations in the Create Campaign page and save the configurations as a campaign template, for future use. The campaign templates provide the ease of reusing specific campaign configurations while creating new campaigns.
Certification Launch
SSM provides the capability to launch a campaign in Preview mode, Active Mode, or to schedule the launch for a later time.
Preview – This will create the campaign in a read-only mode. This allows the person creating the campaign to review the certifications before setting the campaign to an active mode.
Create Now – This will launch and create a campaign in active mode and will be available to the certifiers immediately.
Schedule Later – This will create and perform the campaign multiple times by setting-up the frequency. The frequency can be setup based on your requirements (Minutes, Hourly, Daily, Weekly, or Cron Expression).
Event-based certifications
SSM provides the capability to do an event-based certification. The most common use case is when a user transfers to a new position, a technical rule is fired that launches a certification to the user’s manager. The manager can then review the user’s current access and approve, reject or conditional certify access during the transition period.
Context and Filtering during Review
SSM provides context and filtering options that can be used by certifiers to make more informed decisions about the access they are reviewing.
Progress – Displays the count of items that are pending, need a consultation or are conditionally certified.
High Risk – Displays high-risk items for base accounts, access, roles, and users as well as the percentage of high-risk records.
Low Risk – Displays low-risk records for base accounts, access, roles, and users as well as the percentage of low-risk records.
Out of Band – Displays access that was granted outside of SSM for base accounts and access.
Recently Reviewed in 30 Days – Last reviewed date for base accounts, entitlements, or roles less than or equal to 30 days.
Accounts Inactive for 60 days – Last Login, Last Used on base account greater than 60 days or base account in Inactive or Manually Suspended status.
Last Used – Displays the date of when the base account, entitlement or role was last used.
Last Certified – Displays the date of when the base account, entitlement or role was last certified.
SOD Risks – Displays whether a Separation of Duties (SOD) Risk exists for the respective base account, entitlement, or role.
Outlier – Displays the appropriate outlier analysis details.
Inactive Accounts – Base accounts that are in an inactive state.
Certifier Response Options during Review
SSM provides a two-step certification process where the first step verifies the management or ownership of what is being reviewed. This is a step that allows the certifier to verify they are the correct person to review the access. The second step is where the individual base accounts, entitlements and roles are reviewed.
Step 1: Verify Management or Ownership
Belongs to Me – Accept management or ownership.
Does Not Belong to Me – Reject management or ownership.
Consult – Certifier has chosen to consult another person to review the access.
Terminate – In the case of a user manager certification, the manager can choose to terminate the direct report through SSM.
Decommission – In the case of an entitlement owner certification, the entitlement owner can choose to decommission the entitlement in the application through SSM.
Step 2: Review Access
Approve – Accept and allow access for the base account, entitlement, or role.
Revoke – Reject and deny access for the base account, entitlement, or role.
Consult – Certifier has chosen to consult another person to review the access. The consulted person will be able to go into the certification and Approve, Revoke, Conditionally Certify the line item they were consulted for.
Conditionally Certify – Conditionally Certify the line item until the end date chosen and then revoke task will be generated for the line item conditionally certified. For example, you want a user to retain access to an application until August 31st. On August 31st, the access will be revoked.
Exporting Campaign Results
SSM provided the capability to export the campaign results out to an excel spreadsheet. The campaign export includes all the configuration options for the campaign that was launched, a list of the certifications, and the individual line items that were in each certification with the action taken and comments. This export of data is critical and can be provided as proof of certifying access to internal and external auditors.
Summary
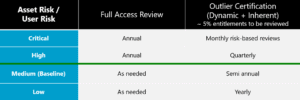
The above matrix is an example of a certification schedule based on Asset Risk / User Risk and weather a Full Access Review or Outlier Certification is being done.
All the access review capabilities in SSM provide organizations with the flexibility to set up certifications that target their most critical apps and beyond that even target the risky or privileged entitlements within those apps. Access review fatigue and rubber stamping happens when managers, application owners or others are asked to certify large amounts of access too often with little or no context. To combat access review fatigue and rubber stamping, we recommend that you take a scaled approach when it comes to the frequency of access reviews and what those access reviews target.
If your organization needs assistance with Saviynt, our expert team can help! Contact us today! Call +1 877 862 1617 or email now.
Read about a recent Saviynt Security Manager deployment here, or check out our webinar recording on “Governing Microsoft Teams with Saviynt Security Manager,” here.